Be it infra, network, or hardware endpoints all of it needs to be protected and secured hence it is very important to adapt to a strong SDLC security posture.
With the help of a strong security posture, the enterprise and its endpoints can be secured and protected from black hat entities. A tested and pragmatic security strategy with efficient implementation is what enterprises need in the ever-changing technological landscape.
The cyber security and infra security processes are handled by dedicated security, info-sec, and IT teams.
These are few key points to ensure a strong security posture:
- Software should have multiple levels of security -> web security, server level security, API level security via API gateway and internal network level security, code level security, and database level security.
- All the servers in the infra need to be well configured and updated all the time, bad implementation or legacy software will result in high-security risks, and legacy hardware and software have a lot of vulnerabilities that can be exploited by black-hats. Legacy hardware is an easy cyber-attack vector.
- Software should have MFA and RBAC well integrated, usually IAM and MFA are mandatory services provided by all major cloud service providers. MFA, RBAC, and IAM ensures a high level of identity and Authorization based security paradigm.
- Strong security strategies have to be in place for the computing layer, storage layer, load balancers, 3rd party integration, 1st party API and 3rd party APIs, DNS, Email server, and multiple other application layer services that are leveraged by the organization.
- The modern-day software solutions are mostly based on the public cloud infra and hence security needs to be tightened up via integrating high-quality security services provided by AWS, Azure, IBM cloud, and other major cyber security vendors.
- WAF and API gateway integration is very vital for strong web and app-level security. It is advised to integrate automated load balancers with the right choice of load balancing algorithm.
- API gateway will take care of TLS offloading, TLS offloading has to be done to make packets smaller in size /discoverable/easy to analyze and stop the IP packets that are being sent from a black hat source.
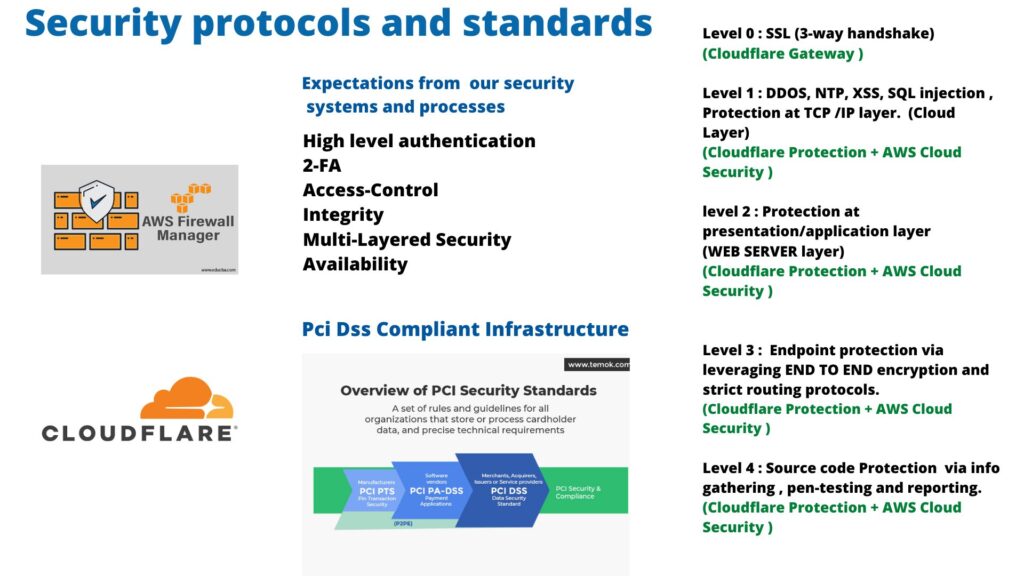
- Cloudflare provides an easy setup that ensures a strong security posture. Integrating Cloudflare enterprise plan will protect IT infra from : DDOS | NTP | XSS | SQL injection | ping of death.
The offline and online infrastructure of a tech organization needs to be protected via effective implementation of a strong security posture, both specialized and integrated services can be leveraged to keep the cloud infra safe and secure at scale.
All the attacks can be mitigated by integrating the right set of 3 rd party security and cybersecurity tools.Integrate high-level authentication via OPEN ID and OAUTHBoth identity management and authorization need to be in place so that the end user can consume the provisioned content in a safer, private, and secure way.
- Keeping the security multiple layers and abstracted, high level of process and data abstraction is also important to keep a robust security posture.
- Higher scalability + high availability is a part and parcel with optimized computing, storage and distribution ops, keep in mind all the components of the system need to be protected, and all the communication needs to be encrypted. Adhering to a good data governance framework is a mandate, without the right set of data management and governance, the system will always be at risk of being hacked and corrupted via first-party and 3 rd party access points.
- SSL (TCP – 3-way handshake) End-to-end point protection via encryption, adapting to efficient encryption strategy is mandatory to keep the internal infra and public infra safe and secure. Ensure that the data transfer between systems must be encrypted and secured via secure data pipeline and data transfer routes.
- The infosec team has to carry out constant security checks, pentest, info gathering, security audits, and data audits and check the physical level security of the offline and online systems in place.
- Both the digital system and the analog systems need to have a strong security strategy in place, all the OSI layers need to have ramped-up security measures to keep all the layers safe, secure, and functional.
- It is not only software but on-prem hardware that needs to be protected both in virtual and physical paradigms.
- Software hacking risks are always there and hardware hacking risk is always there hence both the security vectors be it virtual or physical need to be acknowledged and a strong security posture for both the hardware and software layer needs to be in place to ensure privacy, security, and safety.
- Compliance like PCI DSS, PIC PA -DSS, PCI DSS, PCI security and compliance, GDPR, and HIPAA all need to be adhered upon.
- Both the private and public infra be it cloud / on-prem need to be secured by implementing an effective and tested security strategy.
- To keep the infra and network up and running in an optimized way it is mandatory to integrate the following set of services, the set of services is now divided by all the major cloud service providers plus all these security compliance management software and tools are easy to integrate thanks to the evolving tech and simplified CUI and GUI based experiences.
A high level of security posture can be achieved via the integration of the following set of services :
IAM (identity and access management) | Detection and response system (WAF, IPS, FIREWALLS,) network and application protection framework and tool | Strong data governance policy | Compliance and license management software | security analytics tools | Data protection | API Gateways | Cyber sec tools.
The article above is rendered by integrating outputs of 1 HUMAN AGENT & 3 AI AGENTS, an amalgamation of HGI and AI to serve technology education globally.